Telegram Hidden Cams & More: What You Need To Know In 2024
Is digital privacy truly a myth in the age of relentless connectivity? The proliferation of unsecured networks and the ease with which personal data can be intercepted paints a chilling picture, suggesting that our private moments are increasingly vulnerable.
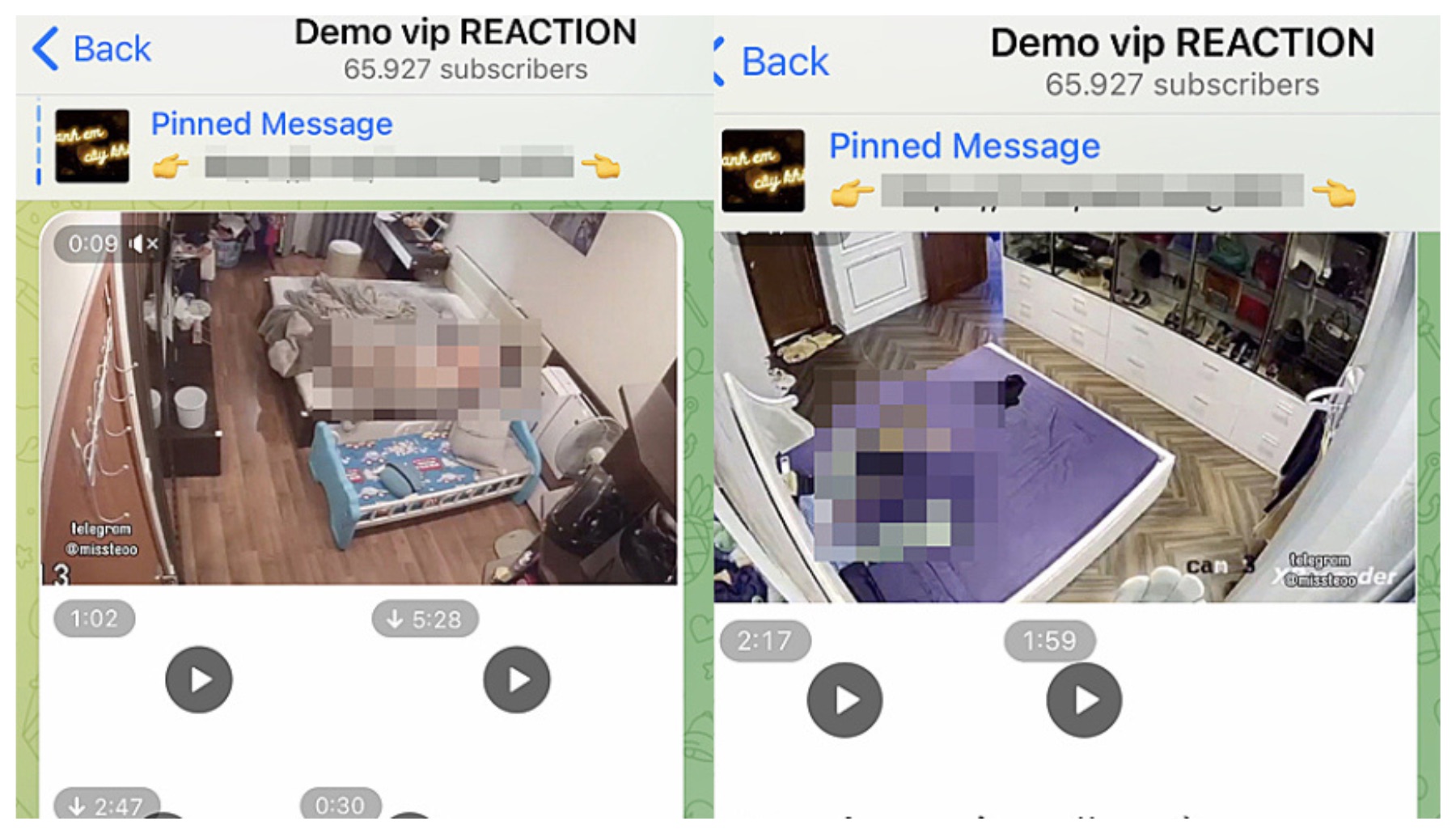
The digital landscape, once envisioned as a realm of liberation and connection, has inadvertently fostered a shadow world where the boundary between public and private blurs. The prevalence of messaging applications, file-sharing platforms, and cloud storage solutions, while offering unparalleled convenience, have also created pathways for unauthorized access. The very tools designed to connect us can be exploited, turning our personal spaces into open books. This is a reality, underscored by the content provided. The mentions of nhm hack camera and @camerasescondidasofc, alongside the phrase "Here are photos and videos of their relatives, taken secretly," hint at a disturbing trend: the surreptitious capture and dissemination of private imagery.
The information points towards an ecosystem where compromising material is readily accessible. The existence of groups like @ipcamsvideos 18+ and related channels on platforms such as Telegram, illustrates how easily such content can circulate. The presence of such groups, with their substantial membership numbers, suggests a demand for these types of materials, creating an environment where exploitation thrives. Further, the use of phrases like "ip cam mom korean ipcam telegram" reveals the targeted nature of these activities, often preying on vulnerable individuals and exploiting intimate moments for profit or malicious intent.
The technical aspects, alluded to in the provided text, add another layer of complexity. The mention of "Home assistant" acting as a proxy, saving images and providing links, indicates attempts to circumvent security measures and obscure the source of these actions. This practice complicates the process of identifying and stopping those who participate in such illicit activities. Furthermore, the references to Telegram bot operating on the same system as the API highlight the sophistication of these operations, demonstrating a level of technical knowledge that facilitates unauthorized access and distribution.
The constant encouragement to "Send message via telegram app," "Open a channel via telegram app," and "You can view and join," points towards an underlying strategy: the seamless integration of these activities into the user experience. This creates an environment where individuals can be unknowingly drawn into illicit networks, making them vulnerable to exploitation or manipulation. Additionally, the repeated references to "Unofficial service for telegram messenger" indicate that this service might be taking advantage of the platform's open nature to facilitate illegal activities.
The following is an example. Since we have no actual person's data we will use a fictional scenario to illustrate how a table might present such information and to illustrate the kind of data a user might be at risk of having compromised. Note that this is a fictional construction for illustrative purposes only:
| Category | Details |
|---|---|
| Full Name | Jane Doe (Fictional) |
| Date of Birth | July 15, 1988 (Fictional) |
| Place of Residence | New York City, NY (Fictional) |
| Social Media Profiles (Potentially Compromised) | Facebook: jane.doe123 (Fictional), Instagram: @janedoe_nyc (Fictional) |
| Email Address | jane.doe@example.com (Fictional) |
| Employment History (Fictional) | Marketing Manager, XYZ Corp. (Fictional) |
| Education | B.A. in Communications, Columbia University (Fictional) |
| Bank Account Information (Hypothetical Risk) | Potentially exposed through phishing or malware attacks, but this information is not present in the initial context. |
| Contact Information (Potentially Compromised) | Phone number (Fictional) (555) 123-4567 |
| Reference Website (For illustrative purposes) | Federal Trade Commission |
The core message of the provided information is a cautionary tale. This content underscores the ongoing need for robust privacy practices and the importance of critically evaluating the digital services we use. The mentions of hidden cams and exclusive 2024 underscore the urgency of safeguarding our privacy in the digital age.
The phrase "Home assistant is running as a proxy, basically accessing the images, saving them and providing a link to the images now saved on home assistant" highlights a key aspect of the digital privacy landscape. While home automation devices and services can offer convenience and control, they often create new vulnerabilities. The information suggests that a user is trusting "Home assistant" to manage and secure images. This reliance introduces a new vector for potential compromise. A breach of the home assistant's security could lead to unauthorized access to personal data, highlighting the risks associated with smart home technology. This also points towards the need for robust security measures, including strong passwords, two-factor authentication, and regular security audits.
The repeated calls to action "Send message via telegram app" are also noteworthy. Telegram, like other messaging apps, presents its own set of privacy concerns. The data is stored on their servers, subject to their own security protocols. Even if the app itself is secure, the metadata, such as the sender, recipient, and time of messages, can be accessed. The frequent use of "Unofficial service for telegram messenger" suggests the use of third-party services. These could be developed by individuals or organizations with less stringent security practices. This increases the risk that personal communications will be monitored or intercepted.
Additionally, the provided content includes references to groups with large membership counts. For example, @ipcamsvideos 18+ @ipcamsvideos 38.6k members. The size of these groups raises questions about the reach and impact of the material they contain. The large numbers are indicative of a network of individuals who are sharing and consuming this content. The existence of large groups like this suggests that these materials are widely circulated.
The repeated line "Here are photos and videos of their relatives, taken secretly" is particularly disturbing. The use of this phrase suggests the potential exploitation of family members, and raises serious ethical questions. This reveals how the violation of privacy can extend beyond an individual. It can extend to family and loved ones, emphasizing the breadth and depth of the harm caused by these activities. Further, the use of the word "secretly" indicates malicious intent and the intentional violation of privacy.
The phrase "We did not find results for: Check spelling or type a new query" highlights another potential issue. It suggests that the searches for this type of content are not always successful, but the continued searches imply a persistent curiosity and a search for something specific. Also, the phrase emphasizes that information may be hard to find, but individuals still look for it.
The presence of the "You are invited to a group chat on telegram" message is also concerning. Being invited to a group is often used to spread information, including malicious links or dangerous ideas, or to attempt to establish a relationship with a person for the purpose of exploitation. It is important to carefully evaluate invitations.
The final line, "This media is not supported in your browser," suggests a technological barrier that could be indicative of attempts to hide or obfuscate the original content. It also serves as a reminder that individuals are not always able to immediately and easily consume media, possibly hindering those who seek to obtain it.
In this environment, the emphasis shifts from merely avoiding bad actors. It's a matter of staying informed, reviewing security settings, and choosing services and apps that prioritize security and privacy. Vigilance is essential, and the onus is on individuals to proactively protect themselves in a world where private moments are increasingly at risk.