Telegram's Hacked Cams: What You Need To Know & How To Stay Safe
Is privacy truly a relic of the past in the digital age? The insidious spread of hacked cameras and the subsequent exploitation of private lives on platforms like Telegram paints a chilling picture of vulnerability, demanding urgent attention.
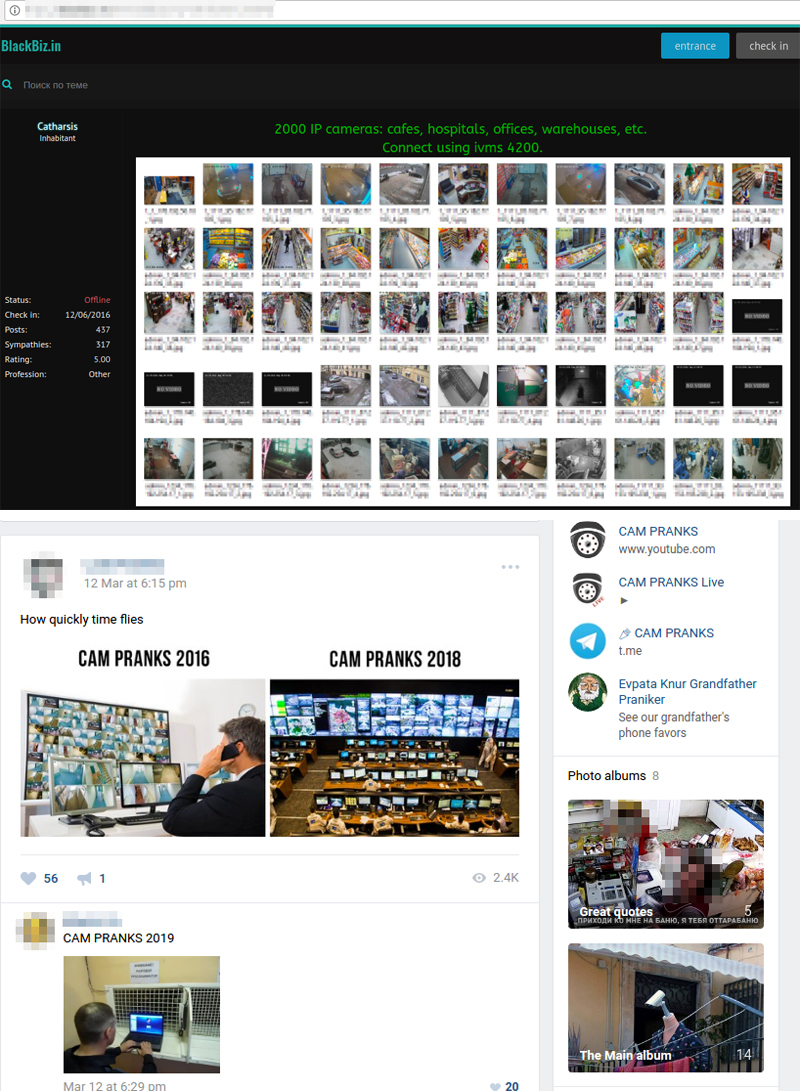
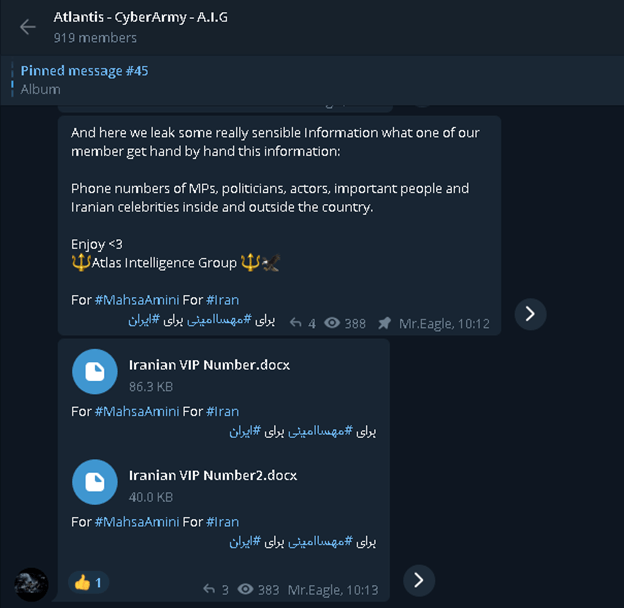
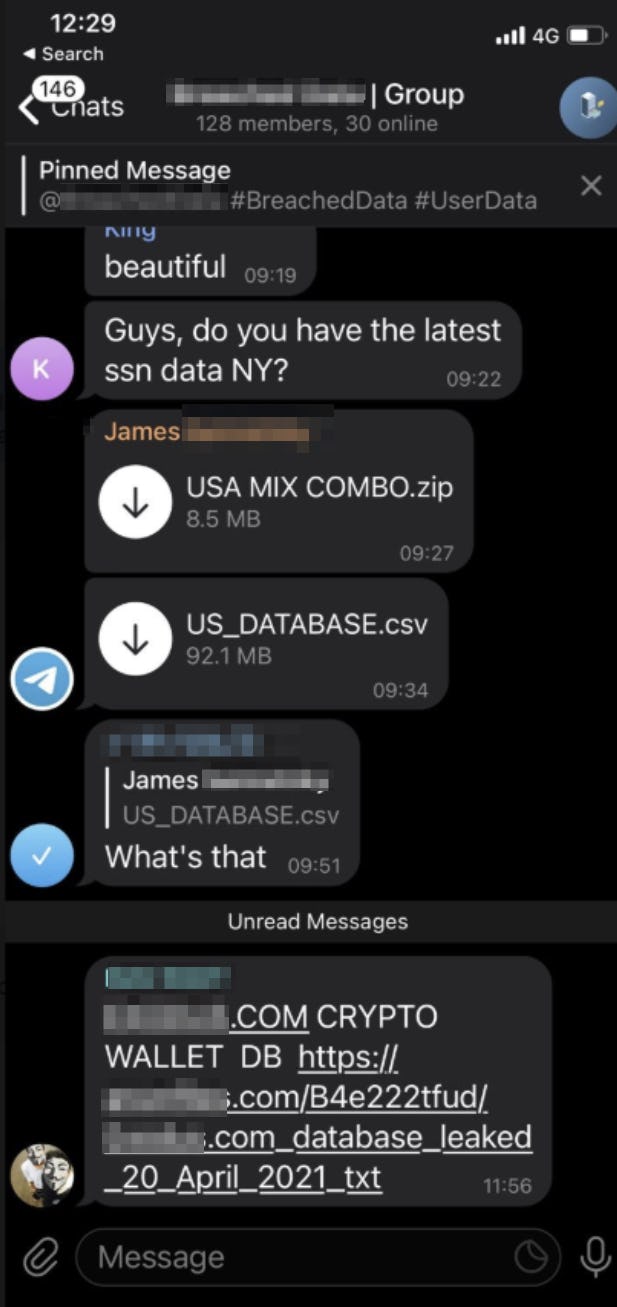
The dark underbelly of the internet, often concealed within encrypted messaging platforms, continues to reveal disturbing trends. Recent investigations have brought to light the existence of Telegram groups specializing in the illicit acquisition and distribution of private footage obtained from hacked cameras. These groups, operating with apparent impunity, exploit the vulnerabilities of everyday technology, turning homes and businesses into potential targets for voyeuristic surveillance and the sale of sensitive material. The implications are far-reaching, impacting not only personal privacy but also raising serious concerns about cybersecurity and the ethical responsibilities of technology providers and platform moderators.
One such discovery involved a researcher named Minh Hung, who stumbled upon a group on Telegram self-identified as experts in breaching private cameras. This group, mirroring numerous others, actively extended invitations, suggesting a network of coordinated illegal activity. The nature of their offerings is particularly troubling: intimate footage harvested from homes and shops across Vietnam, a stark violation of personal boundaries and a clear indication of the scale and scope of this digital crime. The ease with which such groups operate, the public nature of their recruitment, and the direct targeting of innocent individuals highlights the desperate need for enhanced security measures and robust enforcement.
The allure of easy access and potential financial gain fuels the demand for these illicit services. The fact that the platforms themselves often serve as the marketplaces for this illegal trade should raise serious questions. This ecosystem thrives on the exploitation of vulnerabilities, utilizing methods as simple as malicious links to compromise cameras and gain access to real-time surveillance feeds. This poses a serious threat to the security and privacy of ordinary citizens.
The methods used by these hackers are surprisingly straightforward. The use of malicious links to activate and exploit camera systems showcases the need for an urgent public awareness and understanding of the risks.
Adam, a tech journalist with over two decades of experience, offers a nuanced perspective on this issue. His expertise spans a wide range of technological categories, from time-lapse cameras and webcams to drones and 3D scanners, making him uniquely positioned to assess the full impact of this privacy breach. His work underlines the importance of understanding the technology and its potential misuse.
The widespread availability of tools and knowledge required to perform such attacks further exacerbates the problem. Public repositories offer ready-made solutions to those seeking to exploit vulnerabilities, lowering the barrier to entry and accelerating the growth of this insidious threat. These are not merely isolated incidents, they represent a systematic abuse of digital infrastructure.
The focus on Vietnam as a hotspot for this activity reveals a geographical pattern. But it also highlights the global reach of these activities and the need for coordinated international responses to tackle this problem.
The core of this issue centers around the malicious exploitation of IP cameras and their integration into daily life. These devices, often found in homes, offices, and public spaces, can easily be compromised, and these security flaws are exploited by the bad actors.
The Telegram platform itself has become a central hub for these activities. These groups, which openly advertise and distribute illegally obtained footage, operate with minimal restrictions, despite the clear violation of Telegrams terms of service and ethical standards. The failure to adequately police such behavior underscores the need for more responsible content moderation and a proactive approach to the identification and removal of malicious accounts.
These actions often lead to the creation of content for exploitation. The nature of the content is particularly concerning, as it includes intimate footage taken from homes, businesses and medical facilities.
The rise of this illegal industry demands a robust response from law enforcement, tech companies, and users themselves. Enhanced digital literacy, improved cybersecurity measures, and strict enforcement are crucial to mitigate the impact of this digital crime and to protect privacy in the digital age.
The following table provides a summary of the key facts related to the issue:
| Aspect | Details |
|---|---|
| Primary Issue | Exploitation of hacked cameras, distribution of private footage. |
| Platform of Concern | Telegram |
| Geographic Focus (Reported) | Vietnam |
| Targeted Locations | Homes, shops, bedrooms, dressing rooms, toilets, spas, family homes, medical offices, salons, locker rooms |
| Methods Used | Malicious links, exploitation of camera vulnerabilities. |
| Content Type | Private footage, nude videos, intimate scenes. |
| Actors Involved | Hackers, distributors, consumers of illicit footage. |
| Motives | Financial gain, voyeurism. |
| Related Technologies | IP cameras, webcams, smartphones. |
| Recommendations | Enhanced cybersecurity, improved digital literacy, stricter platform moderation, law enforcement. |