Explore IP Camera Channels & Bots On Telegram Now!
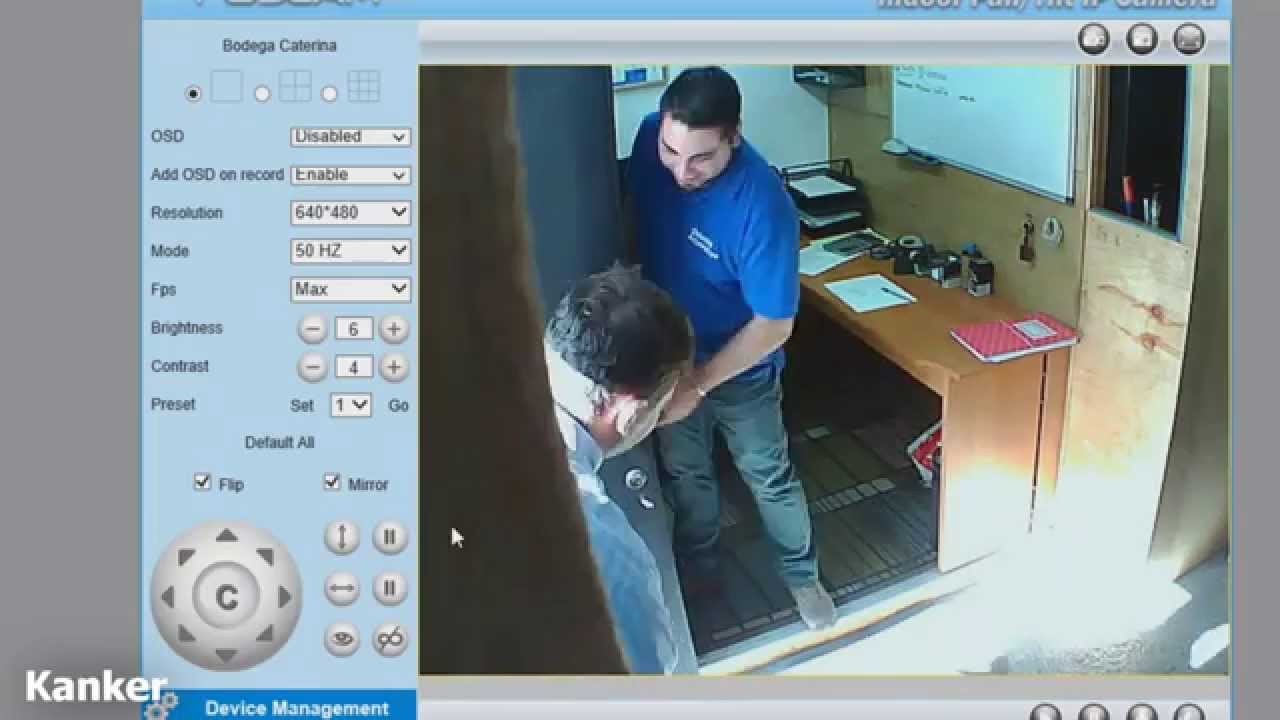
Are your digital eyes truly secure, or are they unwittingly broadcasting a reality you never intended to share? The proliferation of IP cameras, while offering unprecedented convenience and security, has inadvertently created a digital landscape rife with vulnerabilities, making the very technology designed to protect us a potential source of exposure.
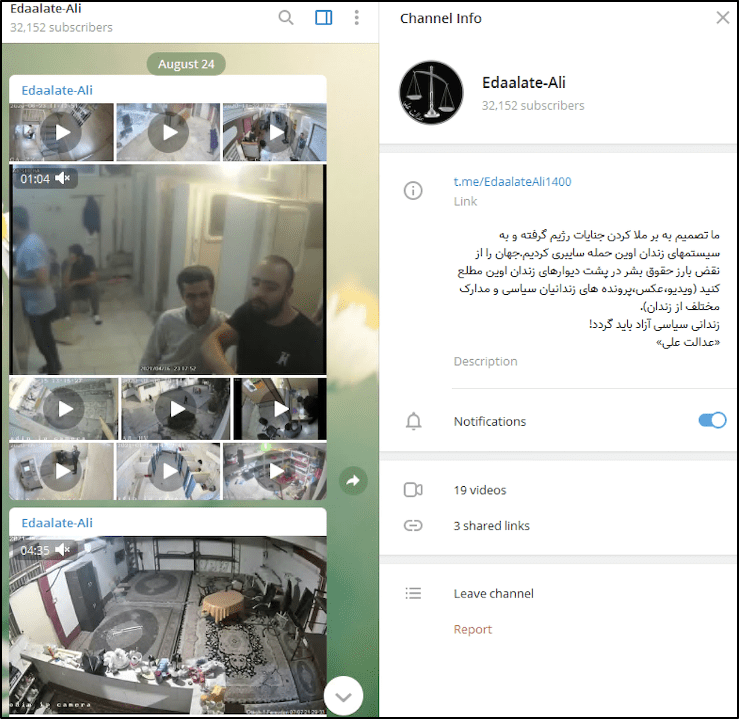
The ease with which one can access and potentially exploit these devices is a growing concern, yet the topic remains relatively obscure to the average user. Various channels and groups on platforms like Telegram, accessible to anyone with a simple search, are dedicated to sharing content from these often-vulnerable cameras. This raises critical questions about privacy, security, and the ethical considerations of using technology in ways it wasn't intended.
The issue isn't just about the technical aspects of hacking. It also involves the human element: our understanding of security protocols and the awareness we have of the risks. Many users might not realize that their default passwords on their IP cameras make them easy targets, or that their network configurations are exposing them to the outside world. The current situation begs the question: are we, as a society, adequately equipped to handle the security challenges posed by the widespread adoption of interconnected devices?
Let's delve into the specific instances we've found and address how they relate to the broader security of IP cameras.
| Aspect | Details | Reference |
|---|---|---|
| Channels and Groups | The search results are grouped into channels, groups, and bots. These platforms serve as hubs where content from IP cameras are featured. The relevance of these channels are also ordered by a search algorithm. | Telegram search function and various third-party Telegram directory websites. |
| Bots | Bots that interface with IP cameras and Telegram, offering the ability to interact with cameras from the messenger app. One particular bot uses Rust. | Information extracted from bot descriptions and user interactions. |
| Content Type | A large amount of content involves security footage, and some channels explicitly forbid illegal content like child pornography. | Channel descriptions and content shared within groups. |
| Accessibility | Many of these channels are readily accessible via Telegram, accessible by a search bar. This means that anyone can find them. | User reviews and Telegram's search functionality. |
| Technology Used | The channels mentioned employ a combination of existing technologies. Rust, an efficient systems programming language, is one. Android phones are also used to host these apps. | Documentation of programming languages and Android-based hardware |
| Search Terms | The search terms used include "ip cameras," "spy cam," and camera-related keywords, leading to the discovery of channels and groups. | Telegram's search features. |
| User Interaction | Users can contact the channels and interact with them directly. Channels are often updated daily. | User comments and channel posting frequency. |
The landscape is complex, a digital echo chamber where vulnerabilities reverberate. A Telegram channel, for example, can be found at @nhomhackcameras, a group dedicated to sharing IP camera content, inviting users to view and potentially join. Similarly, @hacked_ip_cameraa offers a similar service. The channel @camerasdeseguransa provides another example.
Beyond specific channels, the ecosystem around IP cameras on Telegram includes a variety of bots. One such bot, as advertised, serves as an interface between the user's IP camera and the Telegram platform. Developed in Rust and designed to run on an old Android phone using Termux, this bot demonstrates the ingenuity behind these operations and the resourcefulness of individuals working to leverage and utilize them. By connecting with the system of IP cameras and then broadcasting to the Telegram network, they are able to access and relay live camera data to an audience. This functionality is, in effect, creating a distribution network for the contents of the cameras.
Telegram itself is a key platform for these activities. It is a popular messaging application. The existence of various channels and groups dedicated to IP camera content highlights the platform's role as a hub for sharing and discovering this type of information. Users can search and find channels and groups via name or keywords. The availability of detailed analytics and user reviews further enhances the user experience, creating an environment that promotes interaction, information exchange and user involvement.
The prevalence of these channels brings into focus several significant implications. Firstly, privacy is compromised. Unauthorized access to private camera feeds raises significant concerns. Secondly, the potential for misuse extends beyond mere surveillance. The data gathered could be used for malicious purposes. Finally, the presence of this type of content on platforms like Telegram raises ethical questions about content moderation and the responsibilities of platform providers in addressing these issues.
The technical aspects are another key point to explore. The "magic" of IP cameras and Telegram involves exploiting vulnerabilities in these devices. Some cameras have default passwords that are easily guessed or cracked, and some are misconfigured on networks, leaving them accessible to anyone. A search for "ip cameras" quickly reveals various related channels, groups, and bots. Each tab displays information in order of relevance.
Consider the user experience. Telegram directory websites are available for listing channels, groups, and bots. Users can search for channels and groups, with detailed analytics and user reviews. Information about the current environment is provided in an attempt to keep you informed and make the appropriate choices. There are methods for sending messages via the Telegram app. The process involves interacting with existing content and engaging with like-minded people and communities.
We can identify and examine the search term: Spy cam ip qr \ud83d\udcf8 3.2k members. The presence of "QR codes" suggests a method for quick access to the channels, potentially bypassing manual search methods. The number of members, 3.2k, is a tangible measure of the audience, indicating the scale of potential exposure. This example offers a glimpse into the overall landscape.
The content itself varies, ranging from live feeds to recorded footage, sometimes described as "solo videos de camaras de seguridad, nada de cp ni otros" ("solo videos of security cameras, no cp or others"). This statement clarifies that the channels may offer a variety of content. However, the statement about the content being exclusive to security cameras may also be a statement to attract new users.
One of the crucial challenges to overcome is the detection and removal of malicious content. The platforms that these channels exist on need to prioritize the development of robust content moderation systems. As a society, we need to be vigilant in identifying potential vulnerabilities and responding accordingly.
The accessibility of this type of content represents a serious concern. It is not difficult to find channels that offer access to live camera feeds. The presence of the channels shows the potential for the compromise of privacy and the possible misuse of data. The responsibility to protect users remains a key point.
The key here is to educate users on the risks associated with IP cameras. They need to understand how to secure these devices and to create a culture of security. It is also important to consider the legal and ethical aspects of this problem. Laws should be created and enforced to deal with any misuse and exploitation of the vulnerable camera feeds.
To summarize, the issue surrounding IP cameras is more than just the cameras themselves; it is about how they're set up, secured, and used. It's about user awareness, the responsibility of platforms, and the need for comprehensive, up-to-date security measures. Only then can we make certain that the technology meant to safeguard our homes and businesses truly protects us, and not the other way around.