Hidden IP Cam & CCTV Feeds: Discover & Access Via Telegram
Can the ubiquitous eye of the internet truly be considered an open secret, a realm where privacy is a mirage and surveillance is the norm? The proliferation of accessible CCTV feeds, often secured by default settings and vulnerable configurations, creates a digital landscape where the unwary can become unintentional participants in a global network of voyeurism.
The digital age, once heralded as a bastion of individual freedom, has paradoxically become a playground for unseen observers. The very technology designed to protect us, from our homes to our workplaces, has simultaneously created avenues for clandestine viewing, a shadowy world where private moments can be streamed to an unseen audience. This phenomenon, fueled by readily available tools and a lack of robust security protocols, transforms the innocent camera into a potential window into our lives.
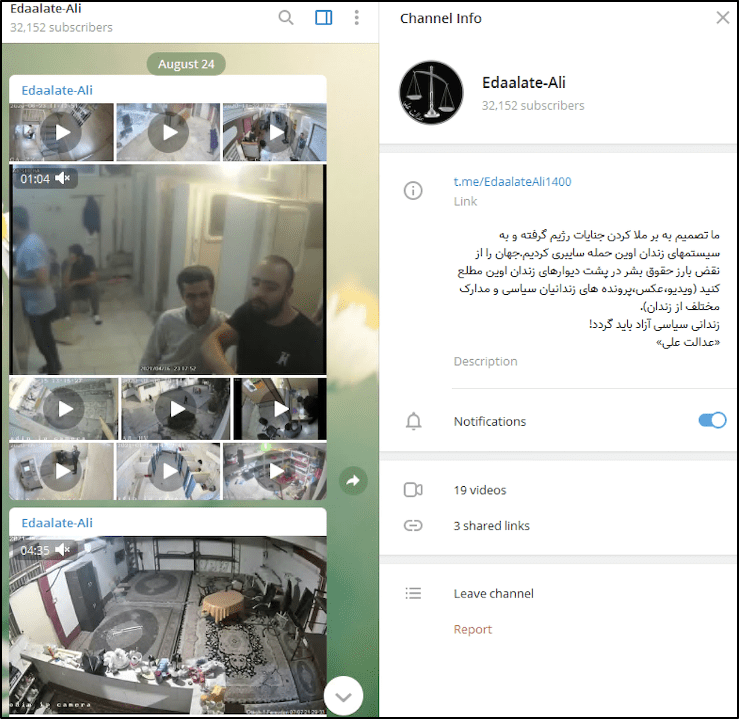
The information landscape reveals a network of channels and groups, primarily accessed via platforms like Telegram, dedicated to sharing and accessing live feeds from various CCTV cameras around the world. These communities, often operating in the grey areas of legality and ethical considerations, offer a glimpse into a world where privacy is not just compromised but actively exploited. The allure of these platforms is a double-edged sword, simultaneously exposing vulnerabilities in our digital infrastructure and attracting a user base that may or may not fully grasp the ethical implications of their actions.
Let's dive into the specifics of this complex issue.
| Aspect | Details |
|---|---|
| Telegram Channels and Groups: | The primary hubs for sharing and accessing live CCTV feeds. Channels like @nhomhackcameras, @spyandcctv, and groups providing QR codes for IP cameras facilitate the exchange of potentially sensitive information. |
| Content Variety: | The content ranges from general security footage to potentially more intrusive views, including footage from changing rooms and other private spaces. Some channels also feature content with explicit themes, highlighting the ethical concerns. |
| Technical Aspects: | The ease of access is largely due to default security settings on many IP cameras and the use of tools like the Shodan API, which allows users to search for and identify connected devices. The Dynamic DNS (DDNS) is sometimes used to solve the problem of dynamic IP addresses. |
| Ethical and Legal Concerns: | The sharing of CCTV feeds raises significant privacy concerns. Viewing, and especially distributing, footage from private cameras without permission raises significant ethical and legal questions. |
| User Engagement: | These channels and groups often boast thousands of subscribers, indicating the significant number of individuals interested in accessing this type of content. Community members seek support, ask for help, and exchange tips for camera types, like Sumpple, Xiaomi, Dahua, Hikvision, and fiscal cameras. |
| Risk of Misuse: | The availability of such feeds increases the risk of malicious actions, including stalking, theft, and the exposure of personal information. |
The core of the issue lies in the intersection of technology and human behavior. The technology itself, the IP cameras and the internet, is neither inherently good nor evil. It's the application of this technology, coupled with the motivations of individuals, that determines the ethical dimensions of this phenomenon.
The inherent vulnerabilities in many IP cameras, coupled with the lack of adequate security protocols, represent a significant problem. Default passwords, unpatched firmware, and the absence of robust encryption render these devices susceptible to unauthorized access. The consequences of this negligence are multifaceted, ranging from the relatively benign such as the unauthorized viewing of a business's security footage to the more severe, including the exposure of individuals' private lives.
The rise of platforms like Telegram has played a crucial role in disseminating this content. Telegram's emphasis on privacy, while commendable in many contexts, also provides a platform for sharing potentially sensitive information. The ease with which channels and groups can be created and the lack of stringent content moderation contribute to the proliferation of unauthorized CCTV feeds. Moreover, the anonymity afforded by Telegram makes it difficult to track down the individuals responsible for sharing and accessing these feeds, further complicating the legal and ethical dimensions of the problem.
Beyond the technical and logistical aspects, there's a critical need to address the human element. The individuals who engage in this activity, who seek out and share these feeds, represent a diverse group. Some may be motivated by simple curiosity, others by a desire to explore the darker corners of the internet, and still others by more malicious intent. Understanding the motivations of these individuals is crucial to developing effective strategies to combat the problem.
The current situation demands a multi-faceted approach. First and foremost, manufacturers of IP cameras must prioritize security. This includes implementing stronger default settings, providing regular firmware updates to address vulnerabilities, and educating users about the importance of securing their devices. Regulatory bodies can also play a crucial role by establishing clear guidelines and standards for IP camera security.
Furthermore, platforms like Telegram must enhance their content moderation efforts. While preserving user privacy is essential, it should not come at the expense of allowing illegal or unethical activities to flourish. Implementing stricter content moderation policies and actively monitoring for the sharing of unauthorized CCTV feeds would be a step in the right direction. Cooperation between platforms, law enforcement, and security researchers would be essential in this regard.
The role of education is another crucial element. Raising awareness among the public about the risks associated with unsecured IP cameras and the ethical implications of accessing and sharing unauthorized footage is vital. Educating individuals about how to secure their devices, choose secure passwords, and enable encryption can significantly reduce their vulnerability.
The legal frameworks surrounding the use of CCTV footage also require careful consideration. Laws regarding privacy and data protection must be updated to reflect the realities of the digital age. Clear guidelines on the collection, storage, and distribution of CCTV footage are essential to ensure that individuals' rights are protected.
The situation also involves international cooperation. Because the internet transcends borders, the sharing of unauthorized CCTV footage can have global implications. International collaboration between law enforcement agencies, cybersecurity experts, and legal professionals is essential to effectively address this issue. This can help facilitate the identification and prosecution of individuals who are involved in illegal activities.
The quest for the most current IP address is a clear indication of the challenges that present in accessing such feeds. IP addresses, are assigned dynamically by Internet Service Providers (ISPs), making it difficult to maintain constant access. Dynamic DNS (DDNS) services offer a workaround for this issue by providing a domain name that automatically updates to the changing IP address, thereby facilitating continuous access to CCTV feeds.
The ecosystem surrounding these accessible feeds consists of a complex network. Participants range from those simply exploring the technical possibilities of accessing CCTV feeds to those with more malicious intents. The channels and groups serve as repositories, holding a variety of footage, often with varying degrees of content.
The use of the Shodan API is another technical element of concern. Shodan, is a search engine for internet-connected devices, including IP cameras. It allows users to search for devices based on various criteria, including manufacturer, location, and open ports. This functionality can be exploited to identify vulnerable cameras, expanding the scope of this issue.
The potential for misuse of these feeds is considerable. The footage from these cameras could easily be used for malicious purposes, including stalking, harassment, or even more serious crimes. This potential for abuse underscores the urgency to address the problem. The ease of access to these cameras could be a serious breach of the individual privacy rights.
The emergence of such communities is not merely a technical issue; it raises fundamental questions about privacy, security, and ethics in the digital age. It presents a stark reminder that technological advancements must be accompanied by an understanding of their potential consequences.
The comments and discussions found in these groups also shed light on the community's desire for help and support, particularly with technical issues related to IP cameras. Members offer advice, request assistance, and share tips for setting up and maintaining their systems, often referencing specific brands and models of cameras, adding another layer to the complexity of the issue. The sharing of experiences, troubleshooting methods, and discussions of various camera types contribute to a collaborative learning environment.
The existence of these channels and groups highlights the importance of individual responsibility and collective action to safeguard privacy. It calls for a multi-layered approach, encompassing security, education, legislation, and international cooperation, to combat the unauthorized access and sharing of CCTV footage.
Addressing this complex situation effectively requires understanding its many aspects. This includes both the technological factors, like the vulnerabilities of IP cameras and the use of tools like the Shodan API, and the human elements, such as the motivations of those accessing and sharing these feeds. This necessitates a collective effort, including manufacturers, platform providers, law enforcement agencies, and individuals, to promote a secure and ethical digital environment.
The need for constant vigilance is underscored by the fluid nature of the online environment. The constant evolution of technology means new methods of accessing and sharing unauthorized CCTV footage will inevitably emerge. The responsibility, therefore, is to adapt, respond and evolve our security protocols, awareness, and legal frameworks to keep up.
The use of certain phrases, such as ip cam mom korean ipcam telegram, suggests the prevalence of content with explicit themes, which adds further depth to the ethical considerations. The existence of such content highlights the need for more stringent moderation policies.
| Topic | Details |
|---|---|
| Common Issues | Accessing IP camera feeds without authorization, using the Shodan API to locate vulnerable cameras, and sharing footage through platforms like Telegram. |
| Affected Parties | Individuals whose private lives are recorded without their knowledge or consent, as well as society at large, as trust and security are eroded. |
| Solutions | Stronger security protocols for IP cameras, more stringent content moderation, education about privacy risks, and updated laws and regulations regarding data protection. |
| Risks | Misuse of footage, including stalking, harassment, identity theft, and the potential for more severe crimes. |
| Challenges | Dynamic IP addresses, the spread of information and content on platforms like Telegram, the anonymity offered by online environments. |
| Conclusion | The access to these channels and groups presents significant ethical and legal concerns. Addressing the issues requires a comprehensive, multi-faceted approach, combining technical solutions, user education, legal frameworks, and ethical considerations. |
The ultimate goal of any solution to this complex problem, the unauthorized access and sharing of CCTV footage, is to maintain a balance between technological advancement and the protection of individual privacy. This requires a proactive, adaptive, and cooperative approach that involves all stakeholders. Only through sustained effort and vigilance can we preserve the integrity of our digital lives.